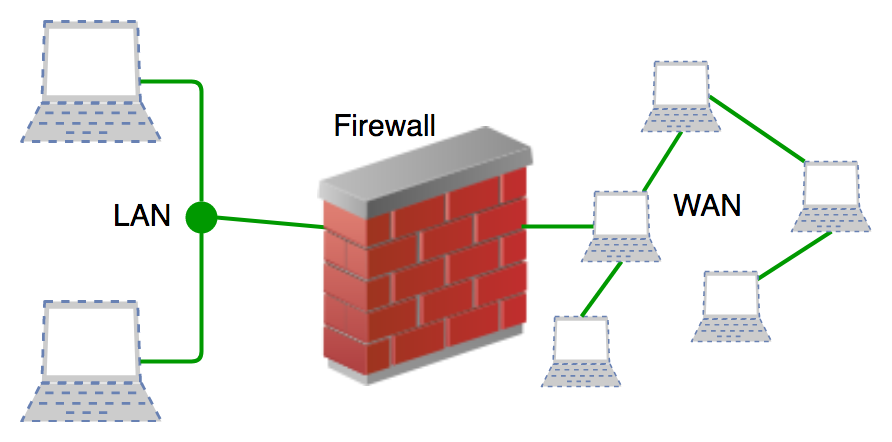
Advanced Firewall Support Techniques for IT Security
Firewalls are a cornerstone of IT security, providing a critical line of defense against cyber threa... read more
Best Firewall Review & Buyers Guide
Best Firewall Review & Buyers GuideFirewall Firm's Firewall Directory consolidates Best F... read more
Vulnerable Web Applications on Developers, Computers Allow Hackers to Bypass Corporate Firewalls
Vulnerable Web Applications on Developers, Computers Allow Hackers to Bypass Corporate FirewallsA ... read more
How to Protect firewalls from hacking?
Firewall security measures are one of the most basic cyber protection tools that organizations of al... read more
Firewall Providers in India
Firewall Providers in India[caption id="attachment_6042" align="aligncenter" w... read more
Why MEDR is Key to Helping Government Combat Stealthy Threats
Managed EDR accelerates cyber response – which is especially important for government agencies und... read more
Enhance enterprise mobility with a business VPN
Reports have suggested that by the year 2020, 50% of the Indian workforce will comprise of millennia...... read more
March 2019’s Most Wanted Malware: Cryptomining Still Dominates Despite Coinhive Closure
Check Point’s latest Global Threat Index sees cryptominers continuing to lead the top malware list... read more
Department of Homeland Security issues security warning for VPN applications — Check Point VPNs not affected
On Friday April 12, The CERT Coordination Center (CERT/CC) with the US Department of Homel... read more
Dragonblood Vulnerability: Is your WiFi secure?
It’s Game of Thrones season! And anything to do with dragons remin... read more
Wi-Fi 6 is for Developers
Wi-Fi 6 is here, and it opens a new chapter in networking. With its enhanced connectivity, the way w... read more
A data breach also means a breach of customer trust
As a business owner, you might be aware of the fact that people only buy from businesses they know, ... read more